x_ctf_b0verfl0w
栈可执行
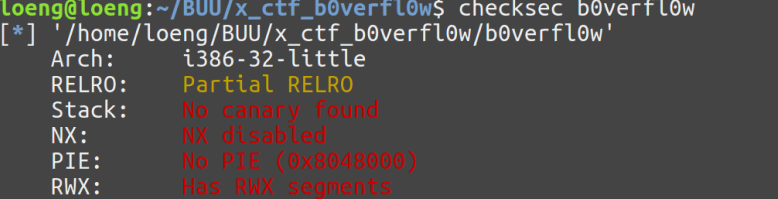
fgets可以输入50个字节,padding就占了32了,还有ebp,ret就剩10字节了,无法写入shellcode,那么我们可以考虑在栈的初始位置布置一段shellcode,然后让程序跳转到栈的起始处执行shellcode
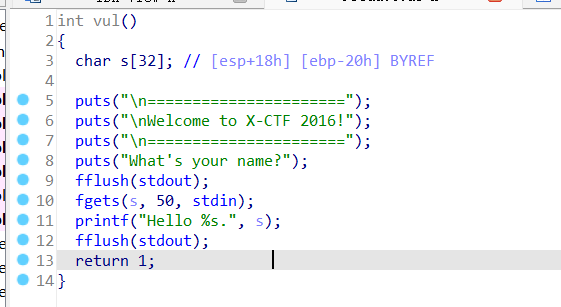
可以看到0x08048504为jmp esp的gadgets
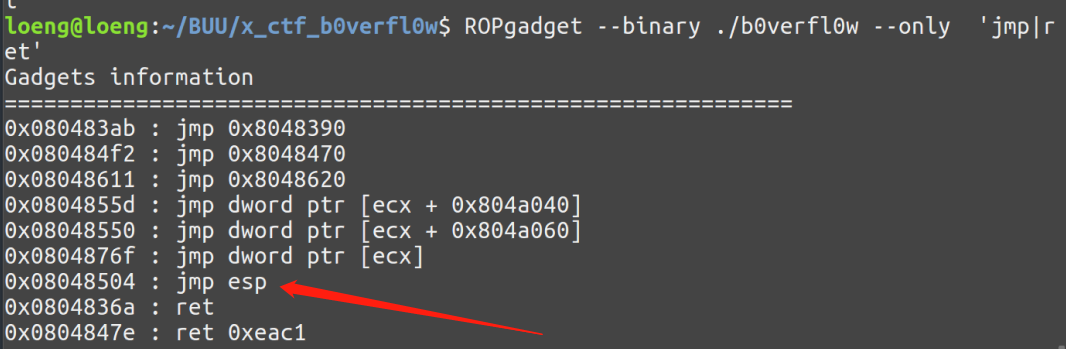
那么payload就可以写成
1 | |
执行jmp esp,同时esp+4,eip指向esp,也就是指向sub esp,0x28;jmp esp,这样就可以劫持esp,跳转执行shellcode
学习点:jmp esp –> esp+4 eip=esp
1 | |