hitcontraining_heapcreator(off_by_one学习)
IDA分析
典型菜单题
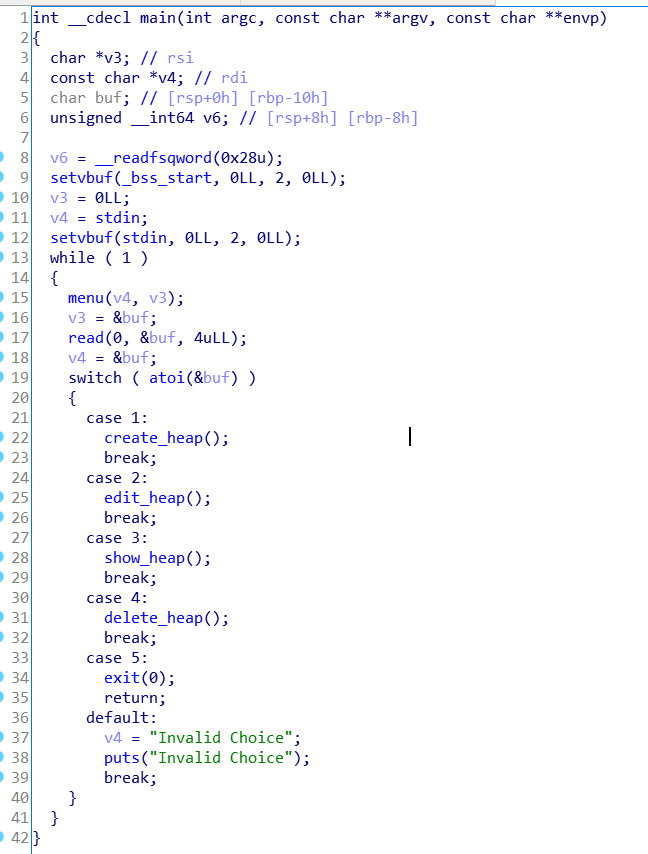
创建堆块
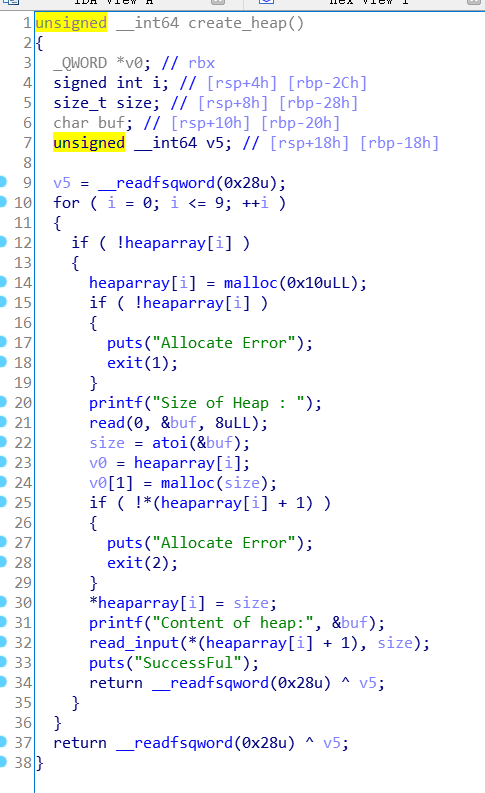
这里heaparray其实就是个一个结构体
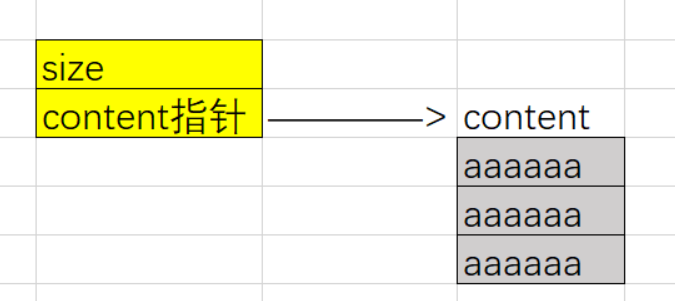
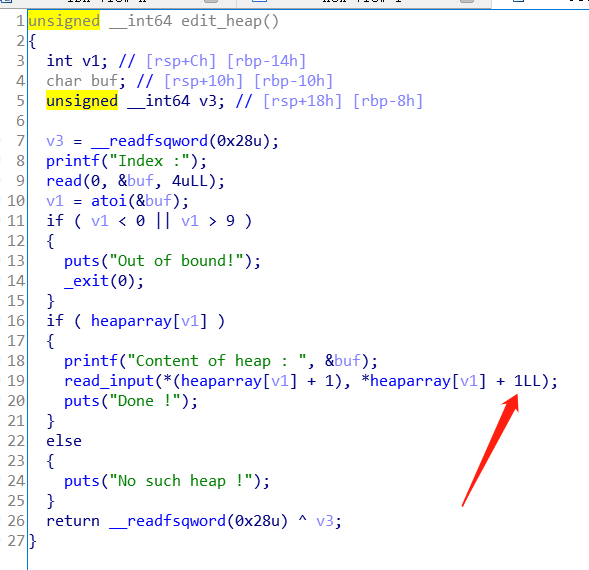
编辑堆块,这里允许填写size+1个字节,存在溢出,考虑off_by_one
打印size和content
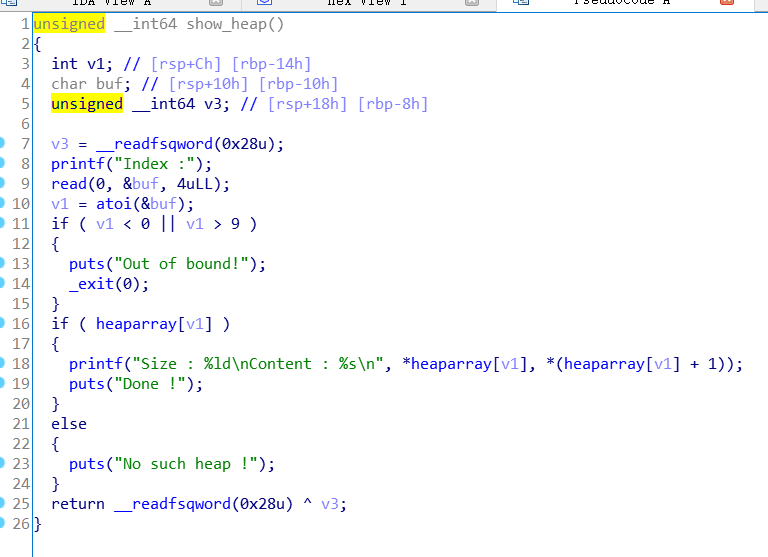
free堆块
调试分析
我们知道chunk的prev_size位在前一个chunk不是free chunk的时候是作为存储前一个chunk的数据的,那我们申请一个0x18的chunk和一个0x10的chunk调试看看
1 | |
可以看到chunk0的数据填满了存储size和content指针的chunk的prev_size位,记得刚刚的edit函数里有个off_by_one漏洞,这样就可以将下一个chunk的size位改了,具体利用看脚本
1 | |
首先申请4个堆块,最后一个堆块写入/bin/sh\x00以便后面使用
1 | |
然后调用edit,通过修改chunk0的content溢出将下一个chunk的size位改成0x81,然后free,这样就后面通过申请0x70字节chunk就能申请回来了,而且content直接覆盖了后面几个chunk
1 | |
我们通过重新申请chunk1,将chunk2的content指针改成free的got地址
1 | |
然后通过show(2)将free got中的地址打印出来就可以得到free的真实地址,然后算出libc base,然后得到system的地址,将system的地址写到free的got表,这样之后调用free函数的时候就变成调用system了
1 | |
最后free掉chunk3,本来是free(binsh的地址)变成system(binsh的地址)也就是system(‘/bin/sh’),这样就可以get shell了
EXP
1 | |