BUU刷题 [Black Watch 入群题]PWN-栈迁移
IDA分析
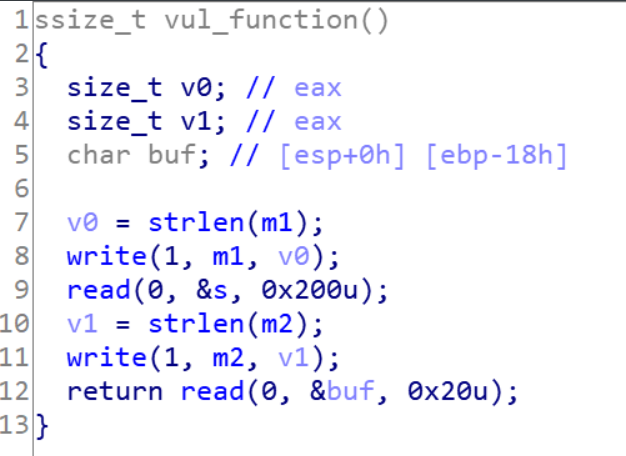
主要功能点就在vul_function()里,第一个read,s在bss段里,虽然可以输入0x200,没法溢出;第二个read只能输入0x20字节,只能覆盖ebp和返回地址,这里发现s在bss段里而且可以输入挺多字节,可以考虑栈迁移到bss段里,但是这题没有提供system和/bin/sh,我们还需要构造ROP链泄露libc,栈迁移知识看我另一篇笔记。
EXP
1 | |
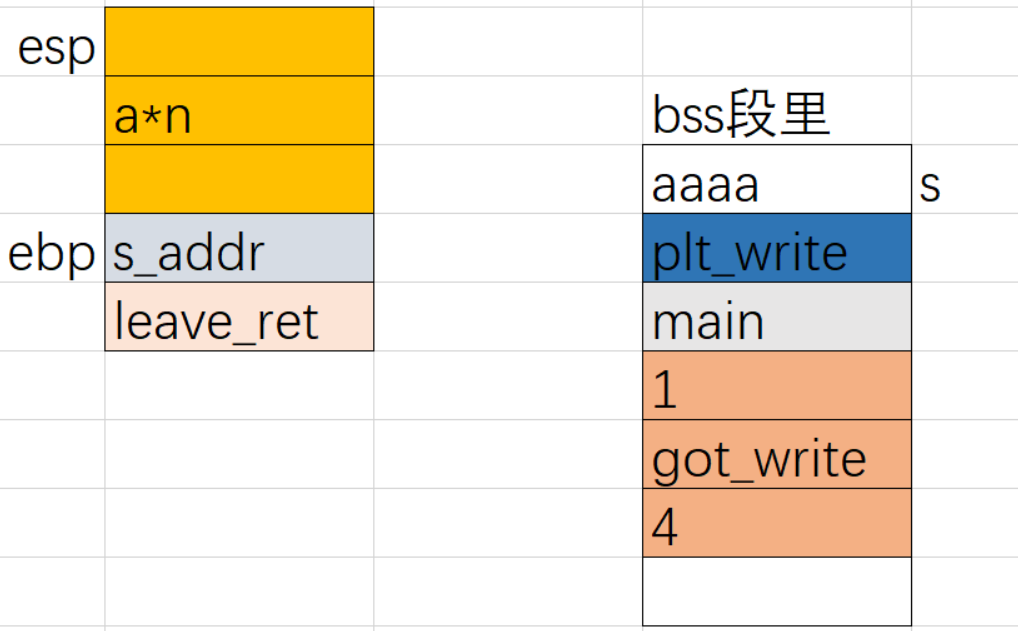
之后就是简单ROP了,完整EXP,掌握了栈迁移就很简单了
1 | |